Intro
Though SIM Swap fraud is a relatively new form of mobile fraud, only dating back as far as 2013, it has become increasingly popular with fraudsters in the UK and around the globe. So much so, that the FBI's 2022 Internet Crime Report recorded losses from SIM Swap fraud of upwards of $72 million dollars, with cases rising by 25% compared to the previous year.
What is SIM Swap fraud?
A SIM swap - also known as SIM porting - is not inherently fraudulent. Telecom providers created this process so that consumers could easily move an existing phone number to a new SIM card. This is helpful in cases where consumers are upgrading to a new phone or replacing a damaged or lost SIM card.

Because this is a data sensitive process, consumers are required to contact their mobile provider, answer questions, and provide account information that verifies their identity before the provider will authorise the SIM Swap.
One of the main attractions of SIM Swap fraud is the simplicity of it. All criminals have to do is to gain some personal information about their potential victim from perhaps social media, purchasing stolen data or via a targeted phishing scam or cyber-attack. They then use this information to get passed the security measures of the victim’s mobile operator, and request that their number is ‘swapped’ to a blank SIM. This can be done by phone, or face-to-face in a high street store.
Once the number has been swapped to the new SIM, the victim’s SIM will be blocked, and scammers will have access to all of their contacts and messages. This could include password reset links and login codes that are sent via SMS to access online banking and other accounts. This is what allows criminals to commit more sophisticated criminal activity, such as theft and identity fraud. What’s more, criminals behind SIM-swap attacks will often sell the personal details they have on their victims on to the dark web, leaving them vulnerable to further attacks in the future.

Many of the major mobile operators in the UK have fallen foul of SIM Swap fraud, as have some of the biggest high street banks. Notable cases of SIM swapping that have made headlines over the past few years include individuals having lost thousands of pounds within the space of an hour, losing all their savings, or having massive loans taken out in their name.
Why is SIM Swap fraud on the increase?
Aside from SIM swap fraud being a relatively easy score for criminals, it is hard for authorities to trace the culprits. Many of the incidents in the UK are thought to be the work of organised crime gangs operating on the dark web, which is notorious for its anonymity. Tracking these gangs down has so far proven to be very difficult.
Social media also has a hand in helping criminals. By monitoring online social activity, it’s easy to identify high value targets, as well as find out personal information that can be used to help answer commonly asked security questions used by mobile operators and banks, such as the name of your first school, first pet or mother’s maiden name.
Finally, and perhaps most importantly, smartphones have evolved from being a convenience to an essential part of everyday life for many of us. It is common for people to have their mobile number linked to their bank account and to use 2 factor authentications when logging in to everything from mobile banking to social media and retail accounts. By stealing someone’s mobile number, you can gain access to many areas of a person’s life, including their financial portfolio.
Read our blog to learn more about why SIM Swapping is on the rise.
The risks of SIM Swap Fraud to Financial Institutions
Over half of the global population own a smartphone, with 98% of adults in the UK owning them. Each of these smartphones provides an access point into the sensitive personal and financial accounts of its owner, and as such increasing opportunity for criminals.
Customers of financial institutions such as banks are generally at the highest risk for SIM swap fraud since this is quite literally "where the money is".
Successful SIM swap operations can make it easy for hackers to obtain things like verification codes and account information, giving criminals a discreet and simple entry point into a person's finances.
On the consumer end, there is limited tools a person has to avoid being a victim of this type of fraud. Instead, it is up to banks, businesses, and mobile operators to prevent fraud from taking place. Fraudulent attacks not only put consumers in jeopardy, but they also damage the reputation of trusted institutions.
How SIM Swap fraud works?
Here is a rundown of how SIM Swap fraud pans out in practice, to help you know exactly what to be vigilant for.
1. The initial port
The first step in a case of SIM Swap fraud is the initial port. This is when the criminal first moves the victim’s phone number onto a mobile device in their control. But how is this achieved?
As we mentioned before, in order for a legitimate SIM Swap to be authorised, a consumer has to first verify their identity with their mobile carrier. This is required before giving anyone the ability to move a number to a new SIM.
Unfortunately criminals have become increasingly adept at sourcing enough information to fool a victim's mobile operator to initiate a SIM swap. So long as they have sufficient information to pass the verification tests (it could even be as simple as having the answers to security questions or a four-digit PIN) they can get permission to port a number to a new SIM in they're control. All the victim will experience is a lack of mobile service, which they might not even be notice, particularly if its done when they're asleep, at work, or using a WiFi connection instead of mobile data.
2. The fraudster gains access to a primary account
Once criminals have successfully gained control of a victims phone number, they’ll generally move quickly onto gaining access to high value accounts as quickly as possible. Most accounts with financial resources tied to them require more than a reset password link or 2FA code to access, though. So, in order to gain access to one of these accounts, the hacker will likely start with a primary account.
An example of a primary account would be a Google account, Apple account, or an email that the rest of a person’s accounts are tied to. With access to one of these primary accounts and a person’s phone number, the hacker can fairly easily get into the rest of the victim’s online accounts.
3. The attacker gains access to an account containing financial resources
Now that the hacker has access to the victim’s primary account, gaining access to the rest of their accounts is relatively simple. All they have to do is go through the password-reset process for the accounts they want to hack into, follow links, and copy verification codes. Once they’ve done this, they’ll have direct access into an account that is tied to the victim’s finances - generally a bank account.
From here, it’s not too difficult to imagine what happens. The victim’s funds are moved into the hacker’s accounts, withdrawals are made, desired goods are purchased, and so on.
Not only does the victim lose some or all of their finances at this point, but they also have lost access to their most valuable online accounts. Recovering these, without their phone number or email address, can be difficult - if not downright impossible.
4. The victim realises what has happened
It might take a few hours, maybe even a day, but at some point the person affected by a fraudulent SIM swap is going to realize that they no longer have access to cellular data or their most valuable online accounts. None of their passwords work, they can’t check their email, and their credit cards are suddenly being declined everywhere.
All they can do at this point is contact their telecom provider and their bank and see what can be done, if anything.
Check the infographic below to see the detailed timeline of SIM Swap and visually understand what happens within the fraudulent period.
How to detect SIM Swap?
While SIM Swap fraud is a serious threat to consumers, it is largely preventable on the business and mobile operator end. Banks and other financial institutions can take measures to protect their customers and their own reputation from the risks of mobile fraud. These precautions include tightening the restrictions on their processes and choosing to operate through security-oriented telecom providers.
One of the most valuable security assets that a bank has at their disposal is the amount of information they have for each of their customers. Any information you have can be used to verify someone's identity. And while a lot of this data can be phished from unsuspecting consumers, some of it is much harder to fake.
An example of this in practice is when a payment card is auto locked after being used in a location far away from the individual's normal routine. Whilst someone that is fraudulently using the card may be able to obtain the legitimate cardholder’s name, and pin, a suspicious change in location can be a telltale sign that the card isn't being used by its intended owner.

The same kind of logic applies to preventing mobile fraud. By working closely with mobile networks, you can use information like an individual's SIM card information, brand of mobile phone, and typical behaviour to verify a person's identity - even after they've had their SIM swapped.
To learn more about how to reduce the risks of SIM Swap Fraud, download our white paper.
Introducing JT SIM Swap Service
We have developed a dedicated platform to mitigate the risks of SIM Swap - a comprehensive SIM monitoring solution that leverage the full market operator coverage to provide real-time information on whether a SIM has been swapped and when. This service allows you as a financial institution or service provider to effectively manage commitments to the secure customer authentication (SCA) part of PSD2 and secure your customers' SMS interactions.
The JT Monitor – SIM swap service provides you with the following
- Easy to integrate API based connectivity
- Ability to manage all clients MSISDNs in one place
- Proprietary logic and systems to manage operator data
- Scheduled checks on MSISDNS every 7 days
- Real-time lookups on subscriber SIM history
Privacy by design approach to manage regulatory changes with a focus on PSD2
How does JT SIM Swap Service work?
Our SIM Swap Service acts as a central, singular point to monitor all of your subscribers' phone numbers.
All use cases for how the data will be used, are pre – approved by operators as the solution provides cross market coverage.
The platform is designed for integration within current workflow tools, so once clients numbers (MSISDNS) are registered on the service, the process of building their SIM swap history begins.
Every seven days, the platform checks each phone number for a recent SIM swap across all operators. Once a number is registered, the history of the number and SIM pairings is created. The service then returns data on whether or not a SIM swap has happened, and specific history elements of when those pairings have been made. This information provides you with the power to verify the customer before continuing to send them sensitive data through SMS.
Each SIM swap and SIM swap check will be timestamped using information from available operators. And in cases where timestamp information isn't available, we'll provide you with a date range between SIM swap checks, giving you an insight into when a SIM swap may have occurred, reducing ‘false positives’ due to frequent checks.
The frequent checks, in turn, provide you with a high level of insight into your SMS operations and, more importantly, your customers' security; reducing exposure to risk and adding a layer of protection for your consumers.
What are the benefits?
- Three API Functions for enhanced control and security
Our SIM swap service comes with three core API functions:
- Add subscriber MSISDNs (phone numbers)
- Live lookup request to determine is a SIM has been swapped, providing history events, date of the last swap and whether a swap has happened
- Remove phone numbers that are inactive or compromised
These three functions combine to give you significantly higher control over your customers' security – and reducing their exposure to risks.
- Always keep accurate subscriber data up to date
Thanks to our frequent SIM swap checks and in-depth data from our operator partners, you'll always have access to accurate and up to date subscriber data. This reduces the likelihood of false positives that may create stumbling blocks for your customers.
- Reduce false positives with frequent phone number checks
Our JT SIM Swap Service checks every MSISDN (phone numbers) in your database every seven days for potential cases of fraud. This frequency is much higher than the market average, which generally only check every few months. The higher than market average frequency enables you to achieve better fraud detection.
- Improved decision making based on richer history from timestamps
Through our JT partner network, with other telecom operators give us access to essential data like timestamps – the exact date and time a SIM and MSISDN were last paired. It means you'll not only know if a SIM swap has occurred but also when did it occur and when did our system detect it. By returning the rich history, clients can then determine how likely it is to be fraudulent.
- Full visibility of subscribers SIM Swap activities through date history
We keep a record of all MSISDN history in our database. In this way, you can easily view subscribers' SIM swap history through the platform, from the moment it was added to the service to the present-day.
- Low cost of entry
Our sophisticated and comprehensive infrastructure makes choosing our SIM swap service a seamless experience. There's no need for you to create additional logic of how porting events are managed across operators, or worry about complex baselining requirements, as all of that will be handled directly by the platform.
Conclusion
SIM swap fraud may be on the rise, but there are solutions available to financial institutions and service providers to help prevent it.
And if you're looking for a complete, reliable and fully managed solution, consider choosing our SIM Swap Service to reduce the risk of fraud for you and your customers today.

To learn more about the offering, please download JT SIM Swap Service product sheet
How JT helps to prevent SIM Swap Fraud with other FPS products?
JT is a global telecoms provider dedicated to providing companies with unique connectivity solutions through mobile networking and emerging technology. Security is at the forefront of our mission. Our services are designed to prevent mobile fraud before it ever happens, keeping consumers safe and preserving the reputations of businesses around the world.
Smartphones are expected to overtake credit and debit cards as the preferred payment method by 2020. Other studies have shown that at least 65% of fraud transactions occurred on mobile devices. It's clear that mobile devices are the future of finance for customers and fraudsters alike, and as such, the need for increased mobile security is greater now than ever before.
JT has created a set of platform-based solutions, providing universal connectivity via a suite of APIs, specially tailored to meet the needs of financial institutions, providing them with the resources they require to keep their customers' data safe. JT's platform-based service acts as an intermediary between a consumer and their bank, providing real-time information that can be used to create a scoring profile within those institutions to enable banks to check for inconsistencies in their client profiles.
Alongside providing clients with a forward-looking connectivity, JT’s solutions provide a suite of tools to detect irregularities and protect clients, that guards against several forms of mobile fraud, including SIM Swapping and call diversion – all driven from the same platform.
1. JT Monitor
JT Monitor is the first part of JT's mobile defense. It provides our clients with SIM level information, making it easy to tell if a SIM Swap has recently occurred. A baseline of SIM data is regularly compared against a SIM's current status, providing users with an insight into how high-risk a consumer is for having had their SIM swapped without their knowledge.

For example, say a customer is attempting to access information or complete a transaction through their bank account. When partnered with JT, that bank can run the request through JT's Monitor system, which checks multiple variables to determine if a SIM is likely to have been swapped maliciously. If JT Monitor determines that the SIM has likely been compromised, it can relay this information to the bank, preventing the hacker from ever accessing any sensitive information or resources within the bank.
JT Monitor works closely with the JT Signal feature as well, which looks for potential call diversions on an individual's phone number - a strong indicator of fraudulent activity. Having these two features working in tandem allows banks to ensure customer safety in spite of the growing risk of SIM Swap fraud.
2. JT Signal
Call forwarding - also known as call diversion - is a form of mobile fraud that routes the phone calls intended for a specific number to another. This means that an institution trying to contact a customer could inadvertently be contacting a fraudster, without the institution's or the customer's knowledge. JT Signal is designed to automatically detect when a forwarded phone call is actually a diverted call and puts a stop to it immediately.
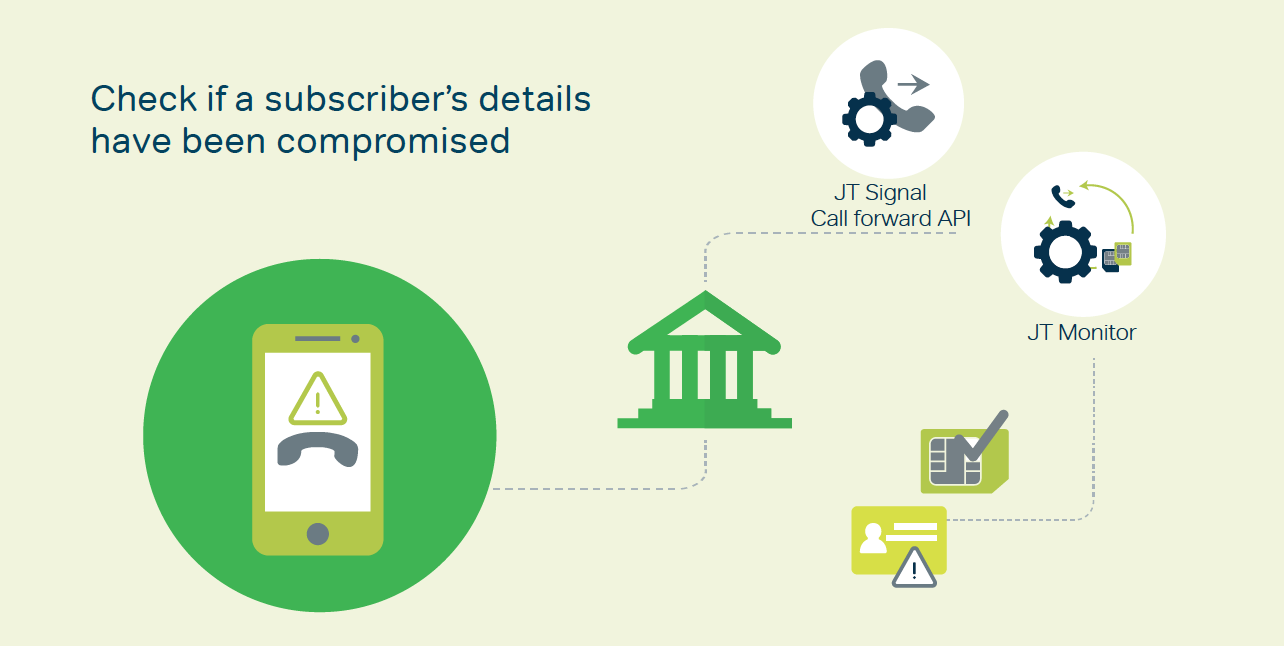
The JT Signal product provides access to a set of APIs that works in conjunction with the JT Monitor product to detect fraudulent SIM Swaps. JT is able to determine whether or not a mobile is set to divert incoming calls. If for example, an unconditional call divert is in place, this can be an indicator that a subscriber’s details may have been compromised, and this will be input to the fraud scoring models of the banks to calculate a level of risk.
As part of the JT Signal product line, the platform can measure other unusual behaviour that will determine whether or not a person's SIM is being used abroad, and if so, where. JT Signal is also capable of determining if a phone number is registered and active, preventing false or outdated information from being used.
3. JT Locate
JT Locate is JT's third set of solutions to enable businesses in their pursuit of combatting fraudulent activity. The JT Fraud platform can provide certain levels of information relating to the location of a subscriber’s handset which again are fed into fraud scoring profiles. Information determining the country a handset is in, which network they are roaming on, along with proximity based on cell tower information.
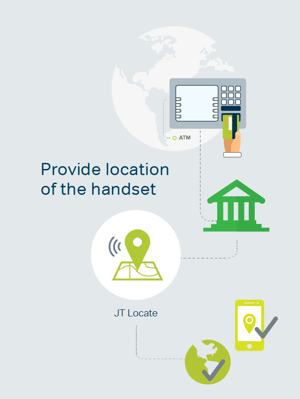
The JT Locate product line, provides these elements of a handsets location to enable customers to determine key information with regards to a subscriber when reviewing account details or making a purchase. For example, if a customer was attempting to make a purchase abroad, their bank would be notified that they were accessing funds in a new location. The bank - partnered with JT - would then send this request through JT Locate's system automatically, which would determine if the subscriber’s handset is in the same country as the access for funds is being made. It would then relay the decision back to the bank, at which point the bank would approve or deny the transaction based on JT's response.
The benefit of the scenario described above is that it takes a safety feature that has existed in banking for several years now and further automates the process, making it more convenient for the customer and the bank. Rather than simply denying a person's transaction because it's in an unusual location, JT Locate can provide intelligence to the financial institution to make a decision on whether or not to approve the transaction. This means that customers can enjoy a better experience when banking abroad, and banks can rest assured knowing that their service is just as secure as before, if not more so.

To learn more about JT Fraud Protection Services,
please check out our FPS product overview.
Or contact us through the below form.







